VL - Escape
Nmap only reveals port 3389/RDP open, when we connect to it without credentials and NLA protocol active:
1
xfreerdp /v:10.10.79.137 -sec-nla
We get welcomed with a conference prompt stating the username KiosUser0, which we can log into with. 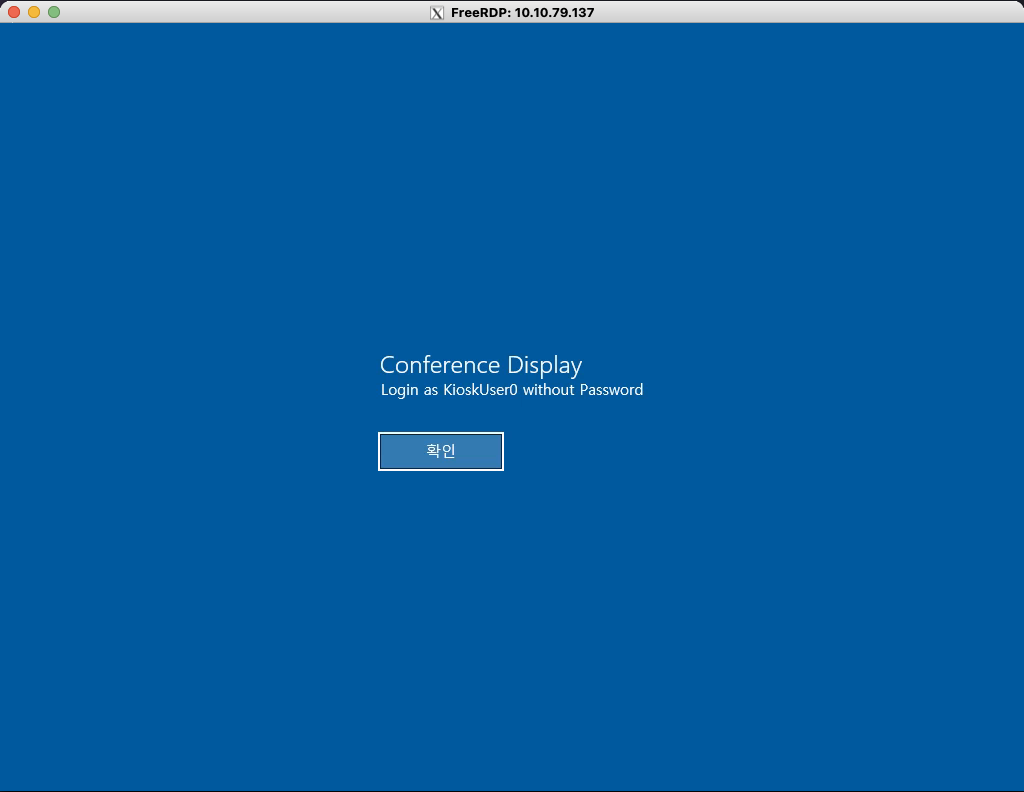 We are in kiosk mode which requires us to find a way to escape, a common method is trying to start the browser and explore the filesystem if other options are locked down. We can start the browser by pressing the Windows key and type msedge and smash enter.
We are in kiosk mode which requires us to find a way to escape, a common method is trying to start the browser and explore the filesystem if other options are locked down. We can start the browser by pressing the Windows key and type msedge and smash enter.  We can now start using different url schemes like
We can now start using different url schemes like file://C:/ to open the local drive, the first noticeable thing is the _admin folder which has a file named profiles.xml with a username and password in it and a flag on the users desktop.
Escaping the kiosk
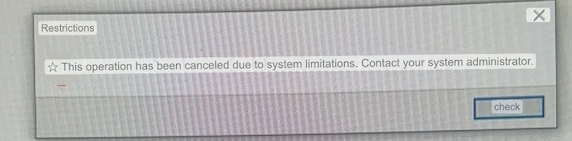
Before we can start using the credentials we still have to find a way to actually escape, we can do this by downloading cmd.exe from the system32 folder: 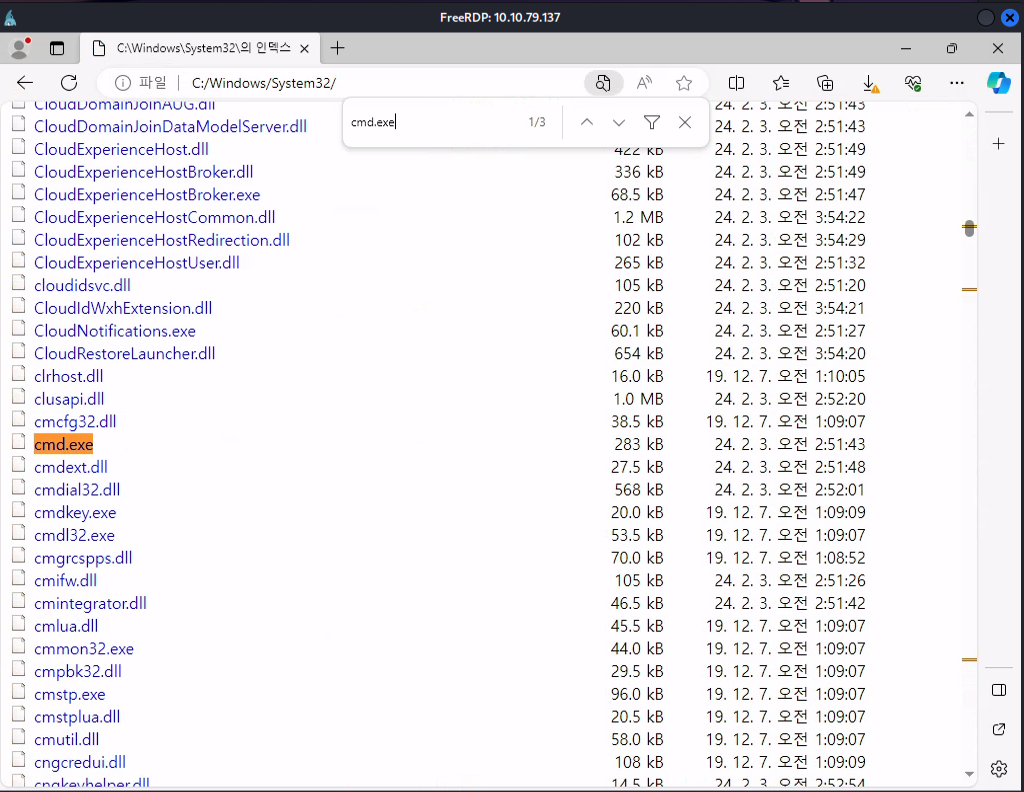 When trying to start the application we get an error in Korean, google translate will be your friend here to discover what the error actually is.
When trying to start the application we get an error in Korean, google translate will be your friend here to discover what the error actually is.
Now we know that we are getting blocked we can try start working around it, one example is changing the filename to something that we know is allowed like msedge, we can change the filename by pressing F2 since the right click is disabled and start cmd.
Remote Desktop Plus
Now we got a working cmd we can start copying the profile earlier to our downloads folder and start the remote desktop plus application located in Program Files (x86). Sadly this does not reveal the password, when googling in the trends of revealing dotted passwords in Remote Desktop Plus we find BulletsPassView on NirSoft (https://www.nirsoft.net/utils/bullets_password_view.html)[BulletsPassword]. We can host this tool on our webserver and curl it to our machine using Powershell.
With this running in the background we can start importing the profile, press the edit button as the main window won’t reveal the password in bulletsPassView and use the password to log in as admin:
1
runas /user:admin cmd.exe
We are now admin but still don’t have the full privileges of Administrator due to UAC, we can start powershell and run the following command to start the prompt:
1
start-process cmd.exe -verb runas